Видео с ютуба Decryption Techniques

7 Cryptography Concepts EVERY Developer Should Know

The Basics of Cryptography and Decryption Techniques

Vigenere CIpher

Encryption - Symmetric Encryption vs Asymmetric Encryption - Cryptography - Practical TLS

How Encryption Works - and How It Can Be Bypassed

Hill Cipher (Decryption)

Vernam cipher||Encryption and Decryption||Example Solution

Encryption and public keys | Internet 101 | Computer Science | Khan Academy

Decrypt using a keyword based transposition cipher

RSA Encryption Explained - Decryption Techniques
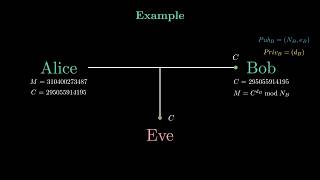
The RSA Encryption Algorithm - How Does It Actually Work + Step-by-Step Example.

Securing Automated Decryption New Cryptography and Techniques

Encryption and decryption methods (FSC)

Encryption & Decryption Techniques for Symmetric Key Cryptography | Private Key Cryptography

Симметричное шифрование: наглядное объяснение #кибербезопасность

Hill Cipher (Encryption)

The RSA Encryption Algorithm (1 of 2: Computing an Example)

What is Encryption?

Rectangular Transposition Encryption and Decryption